- Verifiable links between all deposits and withdrawals
- No obfuscation of origin or destination
- Address hopping completely disabled
Sanctions & Exposure Monitoring
Every deposit and withdrawal undergoes multi-layered screening, with continuous monitoring to detect illicit flows.- Direct and indirect exposure checks: both sanctioned wallets and close counterparties (1-hop) are flagged.
- Cross-chain visibility: suspicious activity across 90+ blockchains is tracked in real time.
- Continuous screening: all flows are checked against OFAC and global sanctions lists.
- Geo-restrictions: access blocked from the U.S., U.K., OFAC-sanctioned, and other high-risk jurisdictions.
Industry Leading Compliance Partners
Elliptic The leading blockchain data and intelligence platform trusted by banks, FIs, governments, crypto native businesses and regulators for compliance, risk management and intelligence operations. Elliptic’s platform has the highest uptime, scalability and response times by a significant margin and supports market leading organizations such as Coinbase, Revolut, Binance and provides Vanish with real-time, multi-asset risk detection for AML compliance. Range On the backend, every transaction passing through Vanish is screened in real time to detect illicit exposure. Trusted by Jupiter, Solana, and PumpFun, Range is one of the leading blockchain security and intelligence platforms — and the market leader in Solana. Range’s screening solution is natively cross-chain, so in addition to performing sanctions checks, it also flags known bad actors from other ecosystems. Backed by their Cross-Chain Explorer, Range currently tracks transactions across 90+ chains to provide complete visibility into asset flows. This is the same technology that underpins the Solana Transaction Security Standard and secures every multisig on Squads Protocol, safeguarding over $20B in assets. Acting as the control tower, Range delivers Vanish real-time screening, KYB/KYT analytics, and continuous sanctions monitoring, ensuring no illicit funds enter or exit the protocol.Real-Time AML Screening & Risk Controls
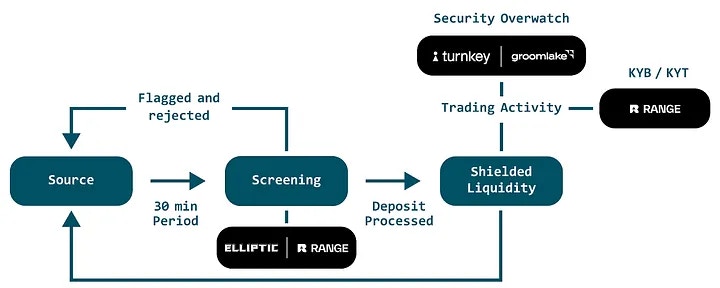
- Every deposit and withdrawal is screened in real time by Elliptic and Range to uphold a clean trading environment and deter illicit activity.
- Continuous checks via Elliptic and Range against OFAC and global sanctions lists detecting fraud and high‑risk wallets.
- Range provides KYB/KYT monitoring to flag high-risk counterparties and suspicious transaction patterns.
- Strict geo-blocking to prevent access from sanctioned or restricted regions.
Vanish’s Security Infrastructure
